|
|
|
Kako podesiti Kohu da radi s LDAP bazom? Video prezentacije o Virtual LDAP-u: http://html5tv.rot13.org/HULK-Virtual_LDAP.html Prezentacija: hulk-Virtual-LDAP.odp Što nam omogućava Koha?
Time dobivamo nove korisnike prvi puta kada se ulogiraju. Kako vidjeti strukturu LDAP baze?ldapvi --host _hostname_:389 -d ldapvi --host _hostname_:389 -d uid=_username_ Logiranje korisnika sa login@ffzg.hrGreška: [Tue Jan 13 23:58:36 2009] opac-user.pl: LDAP Auth rejected : invalid password for user 'mglavica@ffzg.hr'. LDAP error #50: LDAP_INSUFFICIENT_ACCESS [Tue Jan 13 23:58:36 2009] opac-user.pl: # The client does not have sufficient access to perform the requested [Tue Jan 13 23:58:36 2009] opac-user.pl: operation Koha LDAP konfiguracijaProvjeriti verziju
dpavlin@koha-dev:/srv/koha$ grep VERSION /srv/koha/C4/Auth_with_ldap.pm
use vars qw($VERSION @ISA @EXPORT @EXPORT_OK %EXPORT_TAGS $debug);
$VERSION = 3.10; # set the version for version checking
/etc/koha/koha-conf.xml
<ldapserver id="ldapserver" listenref="ldapserver">
<!--
<hostname>ldaps://ldap.ffzg.hr</hostname>
-->
<hostname>ldap://localhost:1389</hostname>
<base>dc=ffzg,dc=hr</base>
<replicate>1</replicate> <!-- add new users from LDAP to Koha database -->
<update>0</update> <!-- update existing users in Koha database -->
<auth_by_bind>1</auth_by_bind>
<principal_name>%s</principal_name> <!-- optional, for auth_by_bind: a printf format to make userPrincipalName from koha userid -->
<mapping> <!-- match koha SQL field names to your LDAP record field names -->
<firstname is="givenname" ></firstname>
<surname is="sn" ></surname>
<address is="ffzg-ml_postanska_adresa_0" ></address>
<!--
<city is="ffzg-prebivaliste_mjesto" ></city>
-->
<city is="ffzg-ml_postanska_adresa_1" ></city>
<zipcode is="ffzg-prebivaliste_postanski_broj"></zipcode>
<branchcode is="local-branch" >FFZG</branchcode>
<userid is="hredupersonuniqueid" ></userid>
<password is="userpassword" ></password>
<email is="mail" ></email>
<categorycode is="local-categorycode" >IMP</categorycode>
<dateofbirth is="ffzg-datum_rodjenja" ></dateofbirth>
<sex is="ffzg-spol" ></sex>
<phone is="ffzg-ml_telefoni_fixed"></phone>
<mobile is="ffzg-ml_telefoni_mobile"></mobile>
</mapping>
</ldapserver>
Koristi LDAP rewrite Da bi sve radilo potrebno je ugasiti ExtendedPatronAttributes na https://10.60.0.252:8443/cgi-bin/koha/admin/preferences.pl?tab=patrons auth as user promjene (prvi pokušaj)Koha konfiguracija skoro radi, osim što je LDAP DN login@ffzg.hr umjesto uid=login,dc=ffzg,dc=hr
Ali, kako se spajamo na pravi ldap.ffzg.hr preko naše proxy skripte koja obogaćuje zapis podacima, i konfiguracijom u /etc/koha/koha-conf.xml
<ldapserver id="ldapserver" listenref="ldapserver">
<hostname>ldaps://ldap.ffzg.hr</hostname>
<base>dc=ffzg,dc=hr</base>
<replicate>1</replicate> <!-- add new users from LDAP to Koha database -->
<update>1</update> <!-- update existing users in Koha database -->
<mapping> <!-- match koha SQL field names to your LDAP record field names -->
<firstname is="givenname" ></firstname>
<surname is="sn" ></surname>
<address is="ffzg-ml_postanska_adresa_0" ></address>
<!--
<city is="ffzg-prebivaliste_mjesto" ></city>
-->
<city is="ffzg-ml_postanska_adresa_1" ></city>
<zipcode is="ffzg-prebivaliste_postanski_broj"></zipcode>
<branchcode is="local-branch" >FFZG</branchcode>
<userid is="hredupersonuniqueid" ></userid>
<password is="userpassword" ></password>
<email is="mail" ></email>
<categorycode is="local-categorycode" >IMP</categorycode>
<dateofbirth is="ffzg-datum_rodjenja" ></dateofbirth>
<sex is="ffzg-spol" ></sex>
<phone is="ffzg-ml_telefoni_fixed"></phone>
<mobile is="ffzg-ml_telefoni_mobile"></mobile>
</mapping>
</ldapserver>
ldaps na upstream LDAPldaps zahtjeva instalaciju IO::Socket::SSL sa sudo apt-get install libio-socket-ssl-perl cardnumber ne dolazi iz ldap-aOsim kod prvog ulogiravanja korisnika kada mu se postavlja isti kao mail izbaciti sve promjene izvan Kohe (TRENUTNO RJEŠENJE)Da bi nam upgrade na novije verzije Kohe bio što jednostavniji, odlučili smo sve LDAP promjene na kraju izbaciti iz Kohe u LDAP rewrite. Koje podatke imamo u LDAP bazi?ovo spada pod osnovne podatke:
* uid - identifikator, korisnicko ime
"Kada cu produzivati korisnicke racune, ja cu svim studentima LinkoviProvjeriti verziju
dpavlin@koha-dev:/srv/koha$ grep VERSION /srv/koha/C4/Auth_with_ldap.pm
use vars qw($VERSION @ISA @EXPORT @EXPORT_OK %EXPORT_TAGS $debug);
$VERSION = 3.10; # set the version for version checking
/etc/koha/koha-conf.xml
<ldapserver id="ldapserver" listenref="ldapserver">
<!--
<hostname>ldaps://ldap.ffzg.hr</hostname>
-->
<hostname>ldap://localhost:1389</hostname>
<base>dc=ffzg,dc=hr</base>
<replicate>1</replicate> <!-- add new users from LDAP to Koha database -->
<update>0</update> <!-- update existing users in Koha database -->
<auth_by_bind>1</auth_by_bind>
<principal_name>%s</principal_name> <!-- optional, for auth_by_bind: a printf format to make userPrincipalName from koha userid -->
<mapping> <!-- match koha SQL field names to your LDAP record field names -->
<firstname is="givenname" ></firstname>
<surname is="sn" ></surname>
<address is="ffzg-ml_postanska_adresa_0" ></address>
<!--
<city is="ffzg-prebivaliste_mjesto" ></city>
-->
<city is="ffzg-ml_postanska_adresa_1" ></city>
<zipcode is="ffzg-prebivaliste_postanski_broj"></zipcode>
<branchcode is="local-branch" >FFZG</branchcode>
<userid is="hredupersonuniqueid" ></userid>
<password is="userpassword" ></password>
<email is="mail" ></email>
<categorycode is="local-categorycode" >IMP</categorycode>
<dateofbirth is="ffzg-datum_rodjenja" ></dateofbirth>
<sex is="ffzg-spol" ></sex>
<phone is="ffzg-ml_telefoni_fixed"></phone>
<mobile is="ffzg-ml_telefoni_mobile"></mobile>
</mapping>
</ldapserver>
Koristi LDAP rewrite Da bi sve radilo potrebno je ugasiti ExtendedPatronAttributes na https://10.60.0.252:8443/cgi-bin/koha/admin/preferences.pl?tab=patrons Za detalje pogledajte LDAP Virtualni LDAP omogućava Kohi da isporučuje podatke preko LDAP-a drugim sustavima, u našem slučaju, kopirkama, vidi SafeQ integration. Drugi dio sustava je LDAP rewrite koji omogućava korištenje login@ffzg.hr bez modifikacija kohe.
upgradeUpgrade na r61 koji ima podršku za novu koha konfiguraciju i logine bez modifikacije kohe: # tunnel dpavlin@llin:~$ ssh -R 8022:localhost:22 10.60.0.252 dpavlin@koha-2010-01-06:~$ cd /srv/virtual-ldap/ dpavlin@koha-2010-01-06:/srv/virtual-ldap$ svn update A sql A sql/organizationalunit.sql A sql/group.sql A sql/hreduperson.sql U lib/LDAP/Virtual.pm U lib/LDAP/Koha.pm U bin/ldap-rewrite.pl Updated to revision 61. start server processdpavlin@koha-upgrade:~$ screen -S virtual-ldap Pokrenuti server (inače to radi monit, ali on je deinstaliran da ne gnjavi) dpavlin@koha-upgrade:~$ cd /srv/virtual-ldap/ dpavlin@koha-upgrade:/srv/virtual-ldap$ ./bin/virtual-ldap.pl LDAP server listening on port 1389 Čudan depdendency koji ne bi trebao postojati (kako radi na produkciji?) dpavlin@koha-upgrade:/srv/virtual-ldap$ ./bin/virtual-ldap.pl Can't locate Net/LDAP/Server.pm in @INC (@INC contains: lib /etc/perl /usr/local/lib/perl/5.10.0 /usr/local/share/perl/5.10.0 /usr/lib/perl5 /usr/share/perl5 /usr/lib/perl/5.10 /usr/share/perl/5.10 /usr/local/lib/site_perl .) at lib/LDAP/Virtual.pm line 12, <DATA> line 96. BEGIN failed--compilation aborted at lib/LDAP/Virtual.pm line 12, <DATA> line 96. Compilation failed in require at ./bin/virtual-ldap.pl line 7, <DATA> line 96. BEGIN failed--compilation aborted at ./bin/virtual-ldap.pl line 7, <DATA> line 96. dpavlin@koha-upgrade:/srv/virtual-ldap$ sudo apt-get install libnet-ldap-server-perl Dio Koha virtual ldap repozitorja: http://svn.rot13.org/index.cgi/virtual-ldap/log/bin/ldap-rewrite.pl
features
start
dpavlin@koha-upgrade:/srv/virtual-ldap$ ./bin/ldap-rewrite.pl
# config = {
"listen" => "localhost:1389",
log_file => "log",
overlay_prefix => "ffzg-",
upstream_ldap => "ldap.ffzg.hr",
upstream_ssl => 1,
yaml_dir => "./yaml/",
} at ./bin/ldap-rewrite.pl line 59.
changes
fetchrss: http://svn.rot13.org/index.cgi/virtual-ldap/rss/bin/ldap-rewrite.pl
Integration of SafeQ and KohaWe are trying to integrate users in SafeQ and our users in Koha. Koha is library system which stores it's users into relational database. To allow SafeQ system access to users we decided to implement LDAP protocol on top of our data scheme in Koha. This is described in little more details at: http://blog.rot13.org/2009/03/integrating_systems_using_netldapserver_and_rdbms.html Mapping configurationUsersExamining UMgr-LDAP.conf configuration we came up with following mapping from our RDBMS to LDAP schema: http://svn.rot13.org/index.cgi/virtual-ldap/view/sql/hreduperson.sql we are creating objectGUID with primary key in our database and rest of the fields should be self-explanatory. This produce following result for LDAP search query: dpavlin@koha-dev:/srv/virtual-ldap$ ldapsearch -h 10.60.0.13 -p 2389 -b dc=ffzg,dc=hr -x 'pager=E00401001F77965C' # extended LDIF # # LDAPv3 # base <dc=ffzg,dc=hr> with scope subtree # filter: pager=E00401001F77965C # requesting: ALL # # dpavlin@ffzg.hr, SURAD, ffzg.hr dn: uid=dpavlin@ffzg.hr,ou=SURAD,dc=ffzg,dc=hr ou: SURAD uid: dpavlin@ffzg.hr objectGUID: 606 cn:: RG9icmljYSBQYXZsaW51xaFpxIc= homeDirectory: /home/606 objectClass: person objectClass: organizationalPerson objectClass: inetOrgPerson objectClass: hrEduPerson memberOf: SURAD sn:: UGF2bGludcWhacSH mail: dpavlin@rot13.org pager: E00401001F77965C givenName: Dobrica displayName:: UGF2bGludcWhacSH # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 This works quite well, and I can see users with their's cards in SafeQ system. 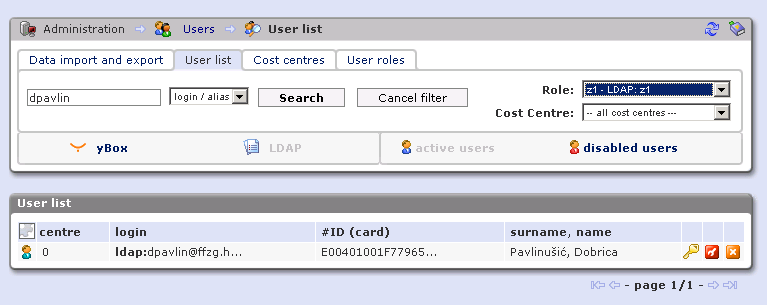 RolesRoles are mapped into groups using following mapping: http://svn.rot13.org/index.cgi/virtual-ldap/view/sql/group.sql Which generate LDAP groups like this:
dn:cn=SURAD,ou=SURAD,dc=ffzg,dc=hr
members: uid=vivainfo,ou=SURAD,dc=ffzg,dc=hr
uid=dpavlin,ou=SURAD,dc=ffzg,dc=hr
ou: SURAD
cn: SURAD
description: Suradnici
objectClass: group
which produce groups in Role drop down:  Some more information about defining groups in ldap can be found at: http://blog.rot13.org/2009/04/ldap_haters_guide_to_groups.html Const centreGroups which we have defined in Koha are really only useful for reporting, so it seems that cost centres in SafeQ are the right place to import our groups. We are trying to use following mapping: http://svn.rot13.org/index.cgi/virtual-ldap/view/sql/organizationalunit.sql Idea is to expose same group data as organizationalUnits in SafeQ so we can get accounting by those groups. We would also like to have different prices for each group of users and ability to report using groups from Koha. Changing configration to: # Mapping of LDAP containers to SafeQ cost centres (departments) # If enabled, all organisational units containers will be displayed in SafeQ as cost centres # If disabled (no, false), attribute mapping is used - see ldap_ou ldap_map_ou = yes We get const centers mapped from our organizational units: 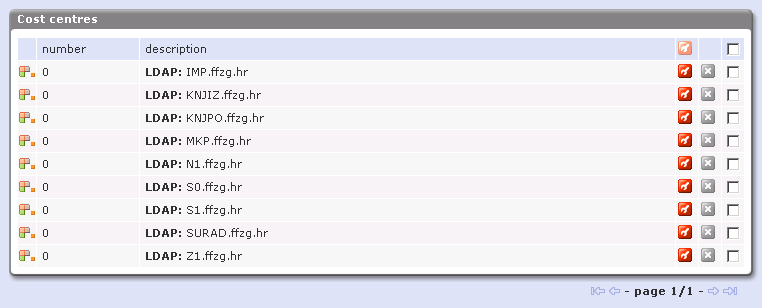 but all const centres have same number (0) How can we supply SafeQ with correct cost center number so users can end up in correct one? Possible bugs in SafeQLDAP searchI also found out something which seems like a bug in the way SafeQ search LDAP server: when you search for 'dpavlin' as login/alias I get following queries:
## filter and [
{ equalityMatch => { assertionValue => "HrEduPerson", attributeDesc => "objectclass" }, },
{ equalityMatch => { assertionValue => "dpavlin%", attributeDesc => "uid" }, },
]
objectclass is o.k., but uid looks like uid=dpavlin% which I think it should be uid=dpavlin* to be correct LDAP syntax. This query doesn't return anything, but next one is o.k.:
## filter and [
{ equalityMatch => { assertionValue => "HrEduPerson", attributeDesc => "objectclass" }, },
{ substrings => { substrings => [{ any => "dpavlin" }], type => "uid" }, },
]
which is uid=*dpavlin* and it finds user. Role/Cost Centere drop-downSelecting role of const center doesn't change filtered output of users. I don't see any difference in LDAP search query when changing selected role and/or cost centar. Is that normal? |
Weblog Archives
|
