Integration of SafeQ and Koha
We are trying to integrate users in SafeQ and our users in Koha. Koha is library system which stores it's users into relational database. To allow SafeQ system access to users we decided to implement LDAP protocol on top of our data scheme in Koha.
This is described in little more details at:
http://blog.rot13.org/2009/03/integrating_systems_using_netldapserver_and_rdbms.html
Mapping configuration
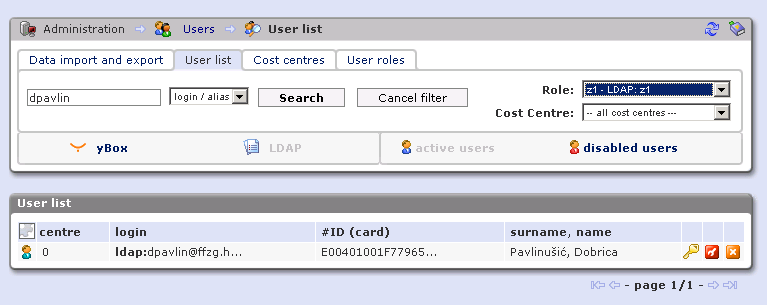
Users
Examining UMgr-LDAP.conf configuration we came up with following mapping from our RDBMS to LDAP schema:
http://svn.rot13.org/index.cgi/virtual-ldap/view/sql/hreduperson.sql
we are creating objectGUID with primary key in our database and rest of the fields should be self-explanatory.
This produce following result for LDAP search query:
dpavlin@koha-dev:/srv/virtual-ldap$ ldapsearch -h 10.60.0.13 -p 2389 -b dc=ffzg,dc=hr -x 'pager=E00401001F77965C' # extended LDIF # # LDAPv3 # base <dc=ffzg,dc=hr> with scope subtree # filter: pager=E00401001F77965C # requesting: ALL # # dpavlin@ffzg.hr, ffzg.hr dn: uid=dpavlin@ffzg.hr,dc=ffzg,dc=hr department: SURAD uid: dpavlin@ffzg.hr objectGUID: 606 cn:: RG9icmljYSBQYXZsaW51xaFpxIc= homeDirectory: /home/606 objectClass: person objectClass: organizationalPerson objectClass: inetOrgPerson objectClass: hrEduPerson memberOf: SURAD sn:: UGF2bGludcWhacSH mail: dpavlin@rot13.org pager: E00401001F77965C givenName: Dobrica displayName:: UGF2bGludcWhacSH # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
This works quite well, and I can see users with their's cards in SafeQ system.
Roles
Possible bug in SafeQ search
I also found out something which seems like a bug in the way SafeQ search LDAP server: when you search for 'dpavlin' as login/alias I get following queries:
## filter and [
{ equalityMatch => { assertionValue => "HrEduPerson", attributeDesc => "objectclass" }, },
{ equalityMatch => { assertionValue => "dpavlin%", attributeDesc => "uid" }, },
]
objectclass is o.k., but uid looks like 'uid=dpavlin%' which I think it should be 'uid=dpavlin*' to be correct LDAP syntax.
This query doesn't return anything, but next one is o.k.:
## filter and [
{ equalityMatch => { assertionValue => "HrEduPerson", attributeDesc => "objectclass" }, },
{ substrings => { substrings => [{ any => "dpavlin" }], type => "uid" }, },
]
which is 'uid=dpavlin' and it finds user.